Support your users with the most secure remote access solution
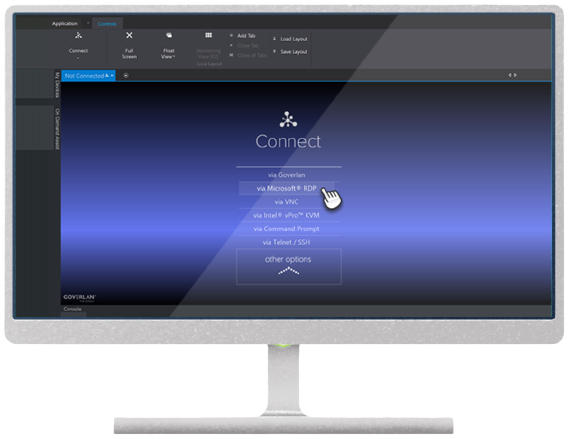
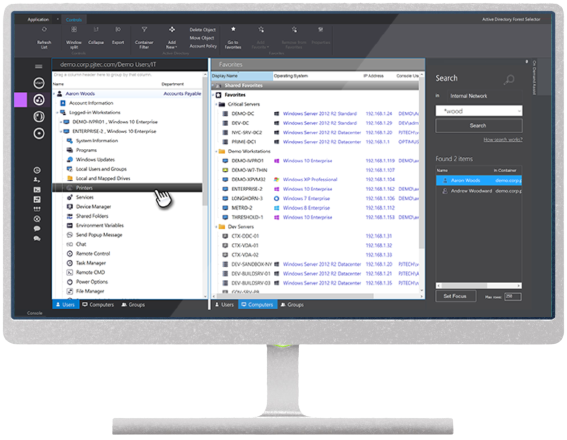
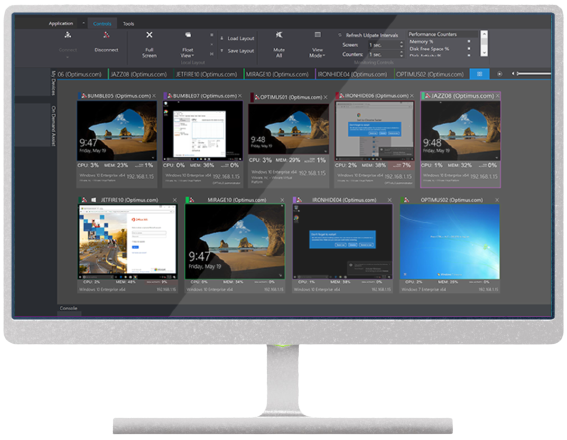
Support your users with the most powerful and secure remote access solution. Our advanced remote desktop technology allows you to you access your users and systems within seconds, no matter where they are. Monitor the screen activity and health status of groups of machines with the multi-machine screen monitor. We support multiple platforms/system types via a range of access protocols including Citrix and Microsoft Terminal Services user sessions.